17 June 2022 by William Estoque
Easy SSL Using AWS Load Balancer
Traditionally, SSL has been set-up within the web server. For nginx, this means copying the certificate to the server and modifying your nginx.conf to point to the certificate. This setup comes with unexpected consequences, not only do you have to do this for each server that you maintain, but now you also have to re-upload the certificate again for all of the server(s) when they are about to expire.
Is there a better solution for this? If you are using AWS for your deployments, why not offload this complexity? Enter SSL using an AWS Load Balancer.
For this solution to work, we will need a structure outlined below:
Request SSL Certificate
The first step to make this work is to create a public SSL certificate in AWS ACM (Certificate Manager). We will use this certificate with our Load Balancer later in the post. A good and important thing when let AWS ACM handle certificates is that they take care of certificate renewals so rest assured that there will be no more downtime due to expiring certificates.
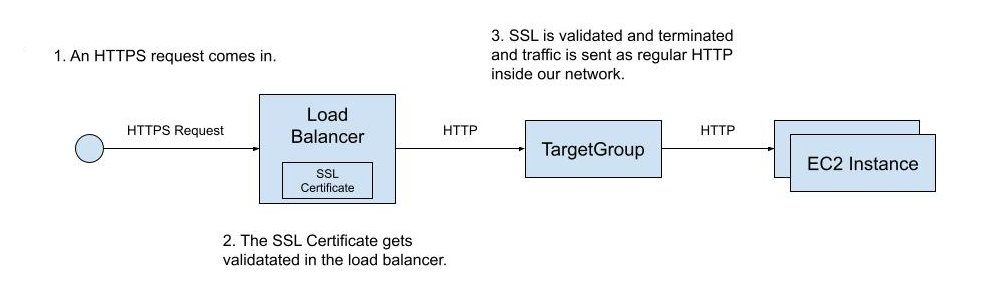
Create a Load Balancer and Target Group
The next step to make this work is to create an AWS Load Balancer. In our example, we will use an AWS ALB (Application Load Balancer) as it is optimized for use with HTTP/HTTPS requests.
Create Application Load Balancer
Start to create a new Load Balancer:
- Under "Load balancer name" put the value sampleapp-alb
- Under "Listeners and routing", click "Create target group"
-
Create a Target Group with
target type of "Instances"
- Have the "Target Group Name" be sampleapp-alb-target-group
- Have the "Protocol" be HTTP
- Have the "Port" be 80
- Add the Instances that you want to be routed. Make sure that port 80 of these instances are reachable.
- Create the ALB using the Target Group we made.
Configure Application Load Balancer
Now that we have created the ALB and it's Target Group. It's time to configure it. We basically want to do 2 things:
- To redirect HTTP requests to HTTPS
- To have HTTPS requests validated with our SSL certificate and then forwarded to the Target Group
To get the behavior mentioned above. Edit the "Listeners" of the load balancer.
Test your changes
To test your changes, get the "DNS Name" of the Load Balancer and use curl or the browser.